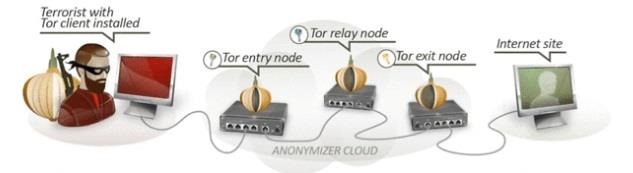
zANTI2 is a new app that came from the Zimperium and Simone Margaritelli, the dSploit author. zANTI comes with a bunch of amazing features, including metasploit exploits, packets sniffing, session and password hijacking and many more. But how do you use them? See this tutorial!
Ready to hack? Let's go.
First off, (if you haven't already), download the zANTI app from dsploit.net
You can register if you want and you're good to go.
Alright, now connect to the WiFi and start scanning.


Wait for the scan to be finished. You will see connected devices with open ports. As you can see on the image above, there are a few devices including one HTC device running Linux (Android) and two printers.
You can now choose which of the devices you want to attack. I will go ahead and select the HTC. If you want to attack all of them, you can select the entire network.
If you open up the device, you'll see a few options popping up.

Firstly, choose which functions do you want to enable during the MITM attack. There is a SSL Strip option, which is very important because it removes the HTTPS protocol by redirecting it to a HTTP. You will not be able to hijack a session when there is a HTTPS protocol so SSL Strip is essential for hacking accounts.
SSL Strip cannot redirect a direct HTTPS, only when victim goes from HTTP to HTTPS. Means that if a victim opens up Facebook (which is HTTPS), SSL Strip will not work as there is a direct request to a HTTPS protocol. I suggest you keeping this enabled the entire time hacking.
Redirect HTTP -
This option redirects a website to another one. Simply choose the URL and enable the function.¨
Replace images -
Choose an image which will be replaced with all the images your victim browses through.
Capture download -
Choose which types you want to capture and enable the function to save all the files your victim downloads. You can also Intercept download by pushing another file to the victim.
Enable the MITM and wait a few whiles. If your victim doesn't use the net (web traffic), you'll have to wait till he/she opens up a browser, downloads a file or just use the network. If everything goes right, a little window saying "IP is vulnerable to MITM attack [or something like that]" should pop up. This means your victim is vunlerable to sniffing, session and password hijacking and many more functions zANTI has to offer.
To see what your victim browses through, see the "logged requests" option. You can also see logged images.

Image above shows logged requests, you can hijack the session by tapping on one of the requests.
To allow each HTTP request individually, use the zPacketEditor. By swyping to the left, you can easily modify the request and send it to the victim.
Alright, now you should know the basics of MITM spoofing attacks, have fun playing!
Just one more thing, always be responsible for what you're doing, don't share private stuff of your victims, After all, it is not that difficult to find out the spoofer across the network.
Ready to hack? Let's go.
First off, (if you haven't already), download the zANTI app from dsploit.net
You can register if you want and you're good to go.
Alright, now connect to the WiFi and start scanning.


Wait for the scan to be finished. You will see connected devices with open ports. As you can see on the image above, there are a few devices including one HTC device running Linux (Android) and two printers.
You can now choose which of the devices you want to attack. I will go ahead and select the HTC. If you want to attack all of them, you can select the entire network.
If you open up the device, you'll see a few options popping up.
- Scan
- Connect to remote port
- Password complexity audit
- MITM
- Vunlerabilities check (shellshock, SSL poodle)
Let's explain them. The scan option will perform another, more advanced scan on the target. You can specify the typea of scan and it will be more accurate on the target.
Connect to remote port is a very interesting option that lets the attacker connect to the open port and estabilish the connection to the victim. If you open up this option, you will see the available ports. In most cases, it would be 80, that is HTTP port. However, there can be more ports available. For example, I attempted to connect to my laptop - I have a password on it, if I didn't have any password set on my laptop, I could easily view everything available in the C:/ drive - pictures, folders, files and many more. Really cool, really spooky; conclusion - secure your laptop with a password, even if there's nobody you know that could possibly break into your device.
We're not done with this option, it brings much more stuff when there is a vunlerability that can be exploited on the victim's PC.
I've found this nice video by Adam Alio demonstrating the power of Zetasploit. He exploits a vulnerability in the victim's PC that allows to connect to remote host via VNC - the virtual network computing, a graphical desktop sharing system that allows to connect to monitor and control your PC using your Android phone, just like as you were running Windows XP.
Then he ran a Cloud exploit and connected to the console. He then took power over the computer and shut it down using shutdown command. Pretty nice and pretty easy. Also pretty scary, isn't it?
Let's skip the password complexity audit and jump right into the MITM section, which will be the most interesting one. MITM stands for man in the middle and what this basically means, is that by triggering an MITM attack, all the traffic goes through your device (you are becoming the man in the middle), thus you can easily view and modify the traffic requests.
To perform this MITM attack, simply select the target and then tap on "Man in the middle" button. A new tab will pop up.

Firstly, choose which functions do you want to enable during the MITM attack. There is a SSL Strip option, which is very important because it removes the HTTPS protocol by redirecting it to a HTTP. You will not be able to hijack a session when there is a HTTPS protocol so SSL Strip is essential for hacking accounts.
SSL Strip cannot redirect a direct HTTPS, only when victim goes from HTTP to HTTPS. Means that if a victim opens up Facebook (which is HTTPS), SSL Strip will not work as there is a direct request to a HTTPS protocol. I suggest you keeping this enabled the entire time hacking.
Redirect HTTP -
This option redirects a website to another one. Simply choose the URL and enable the function.¨
Replace images -
Choose an image which will be replaced with all the images your victim browses through.
Capture download -
Choose which types you want to capture and enable the function to save all the files your victim downloads. You can also Intercept download by pushing another file to the victim.
Enable the MITM and wait a few whiles. If your victim doesn't use the net (web traffic), you'll have to wait till he/she opens up a browser, downloads a file or just use the network. If everything goes right, a little window saying "IP is vulnerable to MITM attack [or something like that]" should pop up. This means your victim is vunlerable to sniffing, session and password hijacking and many more functions zANTI has to offer.
To see what your victim browses through, see the "logged requests" option. You can also see logged images.

Image above shows logged requests, you can hijack the session by tapping on one of the requests.
To allow each HTTP request individually, use the zPacketEditor. By swyping to the left, you can easily modify the request and send it to the victim.
Alright, now you should know the basics of MITM spoofing attacks, have fun playing!
Just one more thing, always be responsible for what you're doing, don't share private stuff of your victims, After all, it is not that difficult to find out the spoofer across the network.